What is Cryptography and why is it Important
Find out how to prevent eavesdroppers from reading your messages.
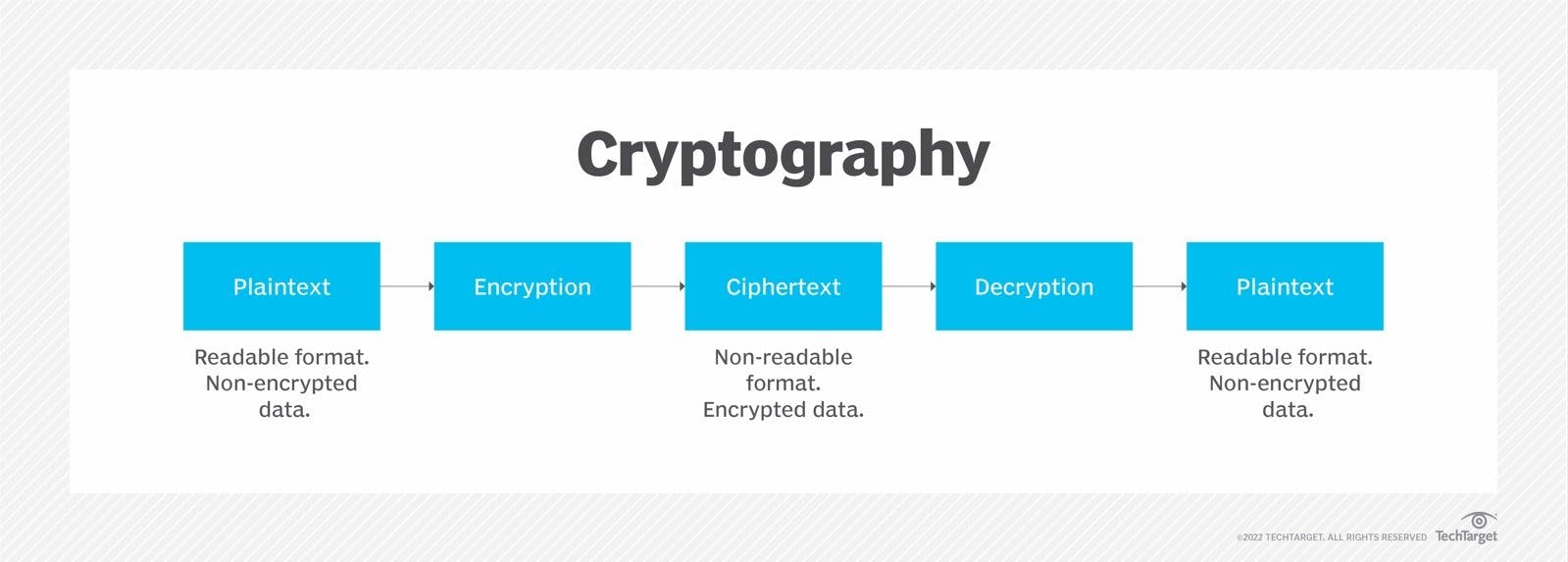
What is Cryptography
In computer science, cryptography refers to secure information and communication techniques derived from mathematical concepts and a set of rule-based calculations called algorithms, to transform messages in ways that are hard to decipher.
Cryptography explained with an example:
Consider the scenario when Lara has to contact her buddy Zain, who is on the other side of the globe. She would prefer that this communication remain confidential and not be disclosed to anyone else. She sends her message over a public network, like WhatsApp. The main objective is to maintain the security of this connection.
 Imagine that a cunning individual by the name of Thanos has covertly obtained illegal access to their line of communication. He can do much more with it than just listen in on their chat because he has access to it. He could, for instance, attempt to change the message or do worse. What would happen if Thanos were to acquire their personal information? The results can be disastrous.
Imagine that a cunning individual by the name of Thanos has covertly obtained illegal access to their line of communication. He can do much more with it than just listen in on their chat because he has access to it. He could, for instance, attempt to change the message or do worse. What would happen if Thanos were to acquire their personal information? The results can be disastrous.
So, how can Lara be certain that her communication with Zain won't be spied on? The use of cryptography is now necessary.
The study and application of methods for protecting data and communication in the presence of adversaries is known as cryptography.
Cryptography Terms
- Encryption: It is the process of locking up information using cryptography. Information that has been locked this way is encrypted.
- Decryption: The process of unlocking the encrypted information using cryptographic techniques.
- Key: A secret like a password used to encrypt and decrypt information. There are a few different types of keys used in cryptography.
- Steganography: It is the science of hiding information from people who would snoop on you. The difference between steganography and encryption is that the would-be snoopers may not be able to tell there’s any hidden information in the first place.
- Plaintext: It is any text humans can read. Sentences and words in English are examples of plaintext. It is plaintext if you can understand what is written simply by reading the text, with no additional decoding.
- Ciphertext: It is a sequence of random characters and numbers illegible to humans. Humans cannot understand cyphertext simply by reading it, and it requires some form of decryption.
Why is it Important
Cryptography is a crucial technique for developing secure systems. Data security, data protection from unauthorized alteration, and data source authentication may all be achieved by the right application of cryptography. Cryptography may also be used to achieve a variety of additional security objectives. Cryptography can provide the following benefits:
Confidentiality means ensuring that no one can read a message except the intended receiver. It also means keeping data secret from those without the proper credentials, even if this data passes through an insecure network.
Integrity (Anti-Tampering) means ensuring the receiver that the received message has not been altered in any way from the original.
Authentication is the process of proving one’s identity. The primary forms of host-to-host authentication on the internet today are name-based or address-based, both of which are notoriously weak. Cryptography can help establish an identity for authentication purposes.
Non-Repudiation. A repudiation is a rejection or denial of something's validity, such as refusing to fulfill a legal contract. Non-repudiation is used in information security to ensure that an individual or organization obligated by contractual obligation cannot deny the authenticity of their signature on the original contract. Non-repudiation refers to mechanisms that prove that the sender sent the message
Encryption and Decryption
Now that we know what cryptography is, let's look at how it can assist secure Lara and Zain's connection.
First, the plaintext version of Claire's message is transformed into an unreadable format. The message is now transformed into random numbers.
 The message is then encrypted using a key (ciphertext).
Lara sends this ciphertext over the communication channel. Suppose, however, that Thanos locates the message and manages to open and alter it before it reaches Zain.
To decrypt the communication and turn the ciphertext into plaintext, which enables him to read it, Zain requires a decryption key.
Using the key, he converts the ciphertext to the corresponding plaintext.
The message is then encrypted using a key (ciphertext).
Lara sends this ciphertext over the communication channel. Suppose, however, that Thanos locates the message and manages to open and alter it before it reaches Zain.
To decrypt the communication and turn the ciphertext into plaintext, which enables him to read it, Zain requires a decryption key.
Using the key, he converts the ciphertext to the corresponding plaintext.
However, he receives an error message as opposed to the original plaintext. This error notice alerts Zain that the message Lara sent and the one he got is different.
Encryption is essential for communicating or sharing information over the network because it allows you to detect and flag tampering.
A technique for hiding the contents of plaintext is encryption. The process of returning ciphertext to its original form is known as decryption.
Types of Cryptography
Symmetric Encryption
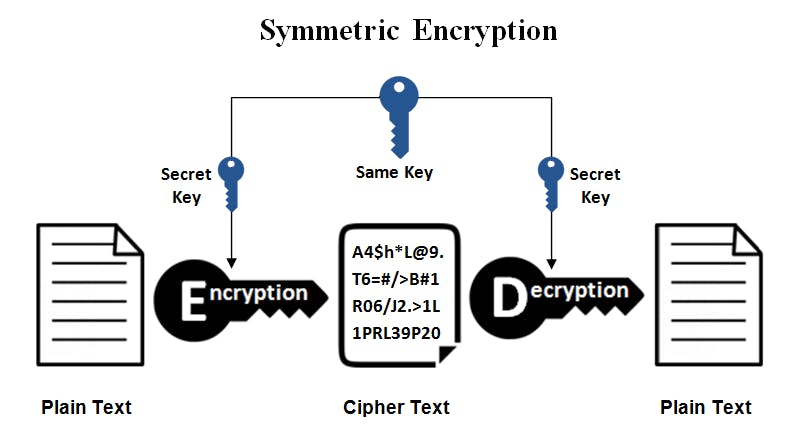 This is the simplest kind of encryption that involves only one secret key to cipher and decipher the information. Symmetric encryption is an old and best-known technique. It uses a secret key that can either be a number, a word, or a string of random letters. It is blended with the plain text of a message to change the content in a particular way. The sender and the recipient should know the secret key that is used to encrypt and decrypt all the messages. Blowfish, AES, RC4, DES, RC5, and RC6 are examples of symmetric encryption. The most widely used symmetric algorithm is AES-128, AES-192, and AES-256.
This is the simplest kind of encryption that involves only one secret key to cipher and decipher the information. Symmetric encryption is an old and best-known technique. It uses a secret key that can either be a number, a word, or a string of random letters. It is blended with the plain text of a message to change the content in a particular way. The sender and the recipient should know the secret key that is used to encrypt and decrypt all the messages. Blowfish, AES, RC4, DES, RC5, and RC6 are examples of symmetric encryption. The most widely used symmetric algorithm is AES-128, AES-192, and AES-256.
The main disadvantage of symmetric key encryption is that all parties involved have to exchange the key used to encrypt the data before they can decrypt it.
Asymmetric Encryption
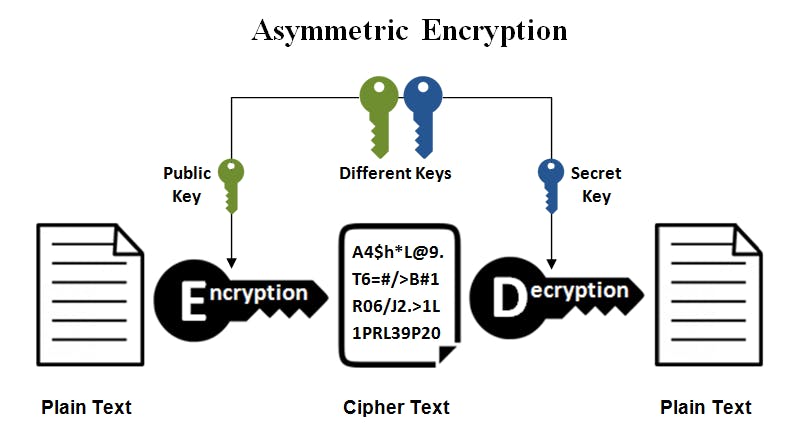 Asymmetric encryption is also known as public key cryptography, which is a relatively new method, compared to symmetric encryption. Asymmetric encryption uses two keys to encrypt plain text. Secret keys are exchanged over the Internet or a large network. It ensures that malicious persons do not misuse the keys. It is important to note that anyone with a secret key can decrypt the message and this is why asymmetric encryption uses two related keys to boost security. A public key is made freely available to anyone who might want to send you a message. The second private key is kept a secret so that you can only know.
Asymmetric encryption is also known as public key cryptography, which is a relatively new method, compared to symmetric encryption. Asymmetric encryption uses two keys to encrypt plain text. Secret keys are exchanged over the Internet or a large network. It ensures that malicious persons do not misuse the keys. It is important to note that anyone with a secret key can decrypt the message and this is why asymmetric encryption uses two related keys to boost security. A public key is made freely available to anyone who might want to send you a message. The second private key is kept a secret so that you can only know.
A message that is encrypted using a public key can only be decrypted using a private key, while also, a message encrypted using a private key can be decrypted using a public key. Security of the public key is not required because it is publicly available and can be passed over the internet. Asymmetric key has far better power in ensuring the security of information transmitted during communication.
Asymmetric encryption is mostly used in day-to-day communication channels, especially over the Internet. Popular asymmetric key encryption algorithm includes ElGamal, RSA, DSA, Elliptic curve techniques, and PKCS.
Difference Between Symmetric and Asymmetric Encryption
- Symmetric encryption uses a single key that needs to be shared among the people who need to receive the message while asymmetric encryption uses a pair of public keys and a private key to encrypt and decrypt messages when communicating.
- Symmetric encryption is an old technique while asymmetric encryption is relatively new.
- Asymmetric encryption was introduced to complement the inherent problem of the need to share the key in the symmetric encryption model, eliminating the need to share the key by using a pair of public-private keys.
- Asymmetric encryption takes relatively more time than symmetric encryption.
Conclusion
When it comes to encryption, the latest schemes may necessarily be the best fit. You should always use the encryption algorithm that is right for the task at hand. As cryptography takes a new shift, new algorithms are being developed in a bid to catch up with the eavesdroppers and secure information to enhance confidentiality. Hackers are bound to make it tough for experts in the coming years, thus expect more from the cryptographic community!
